Security Operations.
Visibility through a single pane of glass to respond quickly and effectively to incidents, while helping to prevent them.
Incident response.
No need to chase down context and evidence when it's all in one place.
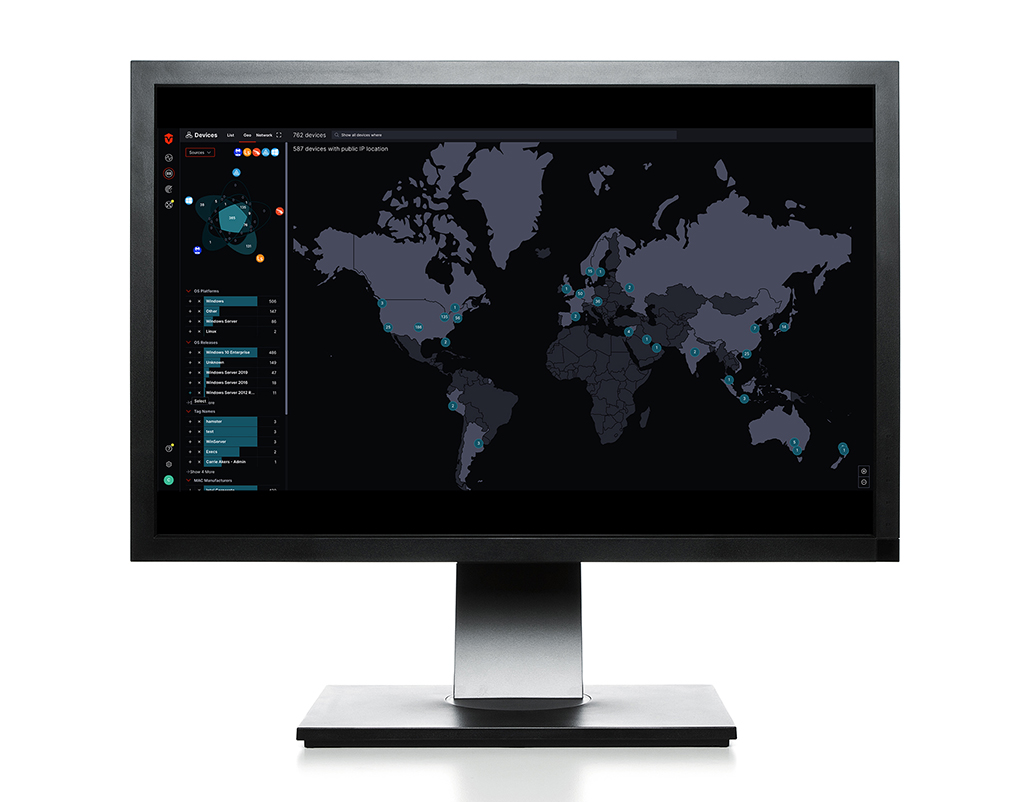
Asset historical context
Access full context and history of any asset to support incident investigations.
Centralized event details
Quickly understand the details of an event through a single pane of glass to reduce impact and downtime.
Real-time asset identification
Quickly identify which assets have been affected in real-time.
Device geolocation tracking
Track the real-time and historical movements of a device with geolocation.
Vulnerability management.
Unknown assets are often underestimated, as are the consequences of doing so.
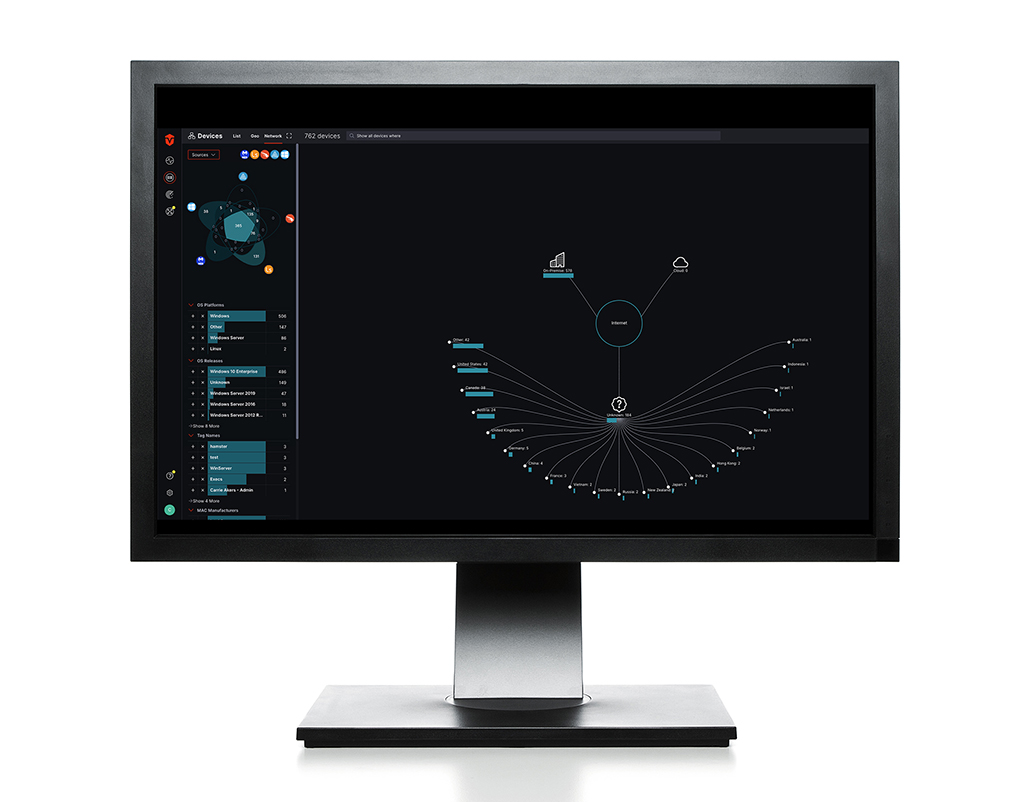
Complete network asset inventory
Identify all known and unknown assets across the network.
Prioritize critical vulnerabilities
Map prioritized vulnerabilities across all assets to assess impact.
Contextualize vulnerabilities
Understand the context of vulnerability by identifying everything affected.
Expedite patching efforts
Prioritize remediation efforts and reduce the time to patch critical vulnerabilities.
Explore other use cases.
How 4D Asset Intelligence helps people in the trenches every day.
What our customers say about us
"If you have a product that’s not properly checking into a console that you’re paying money to secure, then you have a gap. Not only do we check if the application is running, but all the service is running. Unfortunately, that does not guarantee end-to-end compliance without Sevco. Sevco ensures Greenhill can find and close these gaps before they can be exploited by attackers."
Gabe Cioffi, Greenhill Director of Information Technology
"Sevco’s value cannot be overestimated, just one missed device can compromise an entire company."
Grigiory Milias, RFA
"Sevco is a high-impact solution that was quick to configure and delivered extremely quick time-to-value. Having a comprehensive understanding of our assets has really helped us to maximize the investments of my existing tools."
Cecil Pineda, R1 RCMChief Information Security Officer
"Visibility into device inventory is foundational to every security program. It’s challenging to ensure that information stays accurate and updated. Sevco quickly delivers this information to the team and gives us the ability to confidently take action and make informed decisions."
Everett Bates, EverviewChief Information Security Officer
“Sevco gives us the ability to help our customers identify gaps that they did not know existed, giving them an accurate picture of their real attack surface. Partnering with Sevco has delivered immediate value, enabling us to scale quickly and deliver important, foundational security services to our customers across the world.”
Jason Norred, Solutions IIChief Information Security Officer
Previous
Next
The latest in asset intelligence.

CISOs and IT organizations are completely blind to tens of thousands of doors and windows (so to speak) that are wide open for attackers to breach networks and access crown jewel data.

Sevco is helping our customers triage and track resolution of the outages caused by the CrowdStrike update.

Effective remediation requires a high degree of intelligence surrounding assets, from CVEs, operating systems, and applications to identities, endpoint security controls, and IT management controls
Brian Contos, Kathleen Moriarty, and Dr. Chase Cunningham discuss the latest threats, challenges, and new trends in security.

For risk prioritization to be useful for your security and IT teams, it needs to be accurate, timely, and actionable.

In this interview with SafetyDetectives, Greg Fitzgerald, Co-Founder and CXO at Sevco shares how his extensive security background led to co-founding the company.
EXPLORE THE SEVCO PLATFORM
Easy remote setup.
Schedule a one-on-one walkthrough of the platform to see what it can do for you.
AWARDS