Vulnerability Management 2.0:
Why CTEM Is the Future of Cyber Risk Reduction
Why CTEM Is the Future of Cyber Risk Reduction
Introduction
Vulnerability management has long been the cornerstone of enterprise security programs—but today’s complex threat landscape demands more. Traditional vulnerability management tools and practices–built for an era with fewer assets, smaller attack surfaces, and slower changes–are struggling to keep pace with the speed and scale of modern environments and threats.
As cyber risk grows more dynamic and multidimensional, organizations need a smarter, more adaptive approach. Enter Continuous Threat Exposure Management (CTEM)—a framework that promises not only better visibility into risk but also a more effective way to reduce it.
This paper explores the limitations of traditional vulnerability management and how a CTEM program can help organizations transition from reactive patching to proactive exposure reduction.
Five Limitations with Traditional Vulnerability Management
1. Fragmented Tooling and Overwhelming Data
Security teams today operate within highly complex environments, supported by an ever-growing stack of point solutions. While each tool offers valuable insights, the lack of integration makes it difficult to connect the dots. The result? Analysts are inundated with alerts and signals, spending more time interpreting data than fixing issues. At scale, this fragmentation leads to alert fatigue, inefficiency, and missed exposures.
2. Incomplete Asset Visibility
A reliable, up-to-date asset inventory is the foundation of any effective security program. Without it, organizations are flying blind—unsure of what needs to be protected or monitored. This directly impacts the deployment of critical security controls and agents. If you don’t know an asset exists, you can’t protect it—and you can’t identify the exposures that may already exist on it. This creates blind spots in your environment that attackers can exploit, often without needing a known CVE. Shadow assets, end-of-life and orphaned systems, and unmanaged devices all represent potential entry points that go unchecked in traditional vulnerability management programs.
3. Inability to Prioritize Risk Effectively
The number of published CVEs has exploded in recent years. Security teams are expected to triage and remediate thousands of vulnerabilities, but traditional prioritization models—often reliant on CVSS scores—lack business context. Not all high-severity CVEs matter equally. Without factoring in exploitability, asset criticality, and business-specific operational impact, teams waste time on low-priority vulnerabilities while critical exposures linger.
4. Exposures Are Broader Than CVEs
Traditionally, vulnerability management has focused on software bugs, but today’s attack surface is far more expansive. From misconfigured cloud environments to exposed identities and missing security controls, the true scope of exposure goes well beyond CVEs. Focusing narrowly on software vulnerabilities leaves critical gaps in an organization’s defensive posture.
5. Broken Remediation and Feedback Loops
Even when vulnerabilities are identified and assigned, remediation often falls through the cracks. Ownership is unclear—different teams may manage different assets, and handoffs between security and IT are slow or inconsistent. Worse, when fixes are applied, validation is rarely automated. Without a feedback loop to confirm whether an issue has been resolved, organizations are left with a false sense of security.
How Continuous Threat Exposure Management (CTEM) Solves These Challenges
A CTEM program introduces a modern, structured, and continuous approach to reducing risk by managing exposures—not just vulnerabilities. Defined by Gartner, CTEM consists of five phases:
- Scoping
- Discovery
- Prioritization
- Validation
- Mobilization
Here’s how this framework addresses the core issues of traditional vulnerability management:
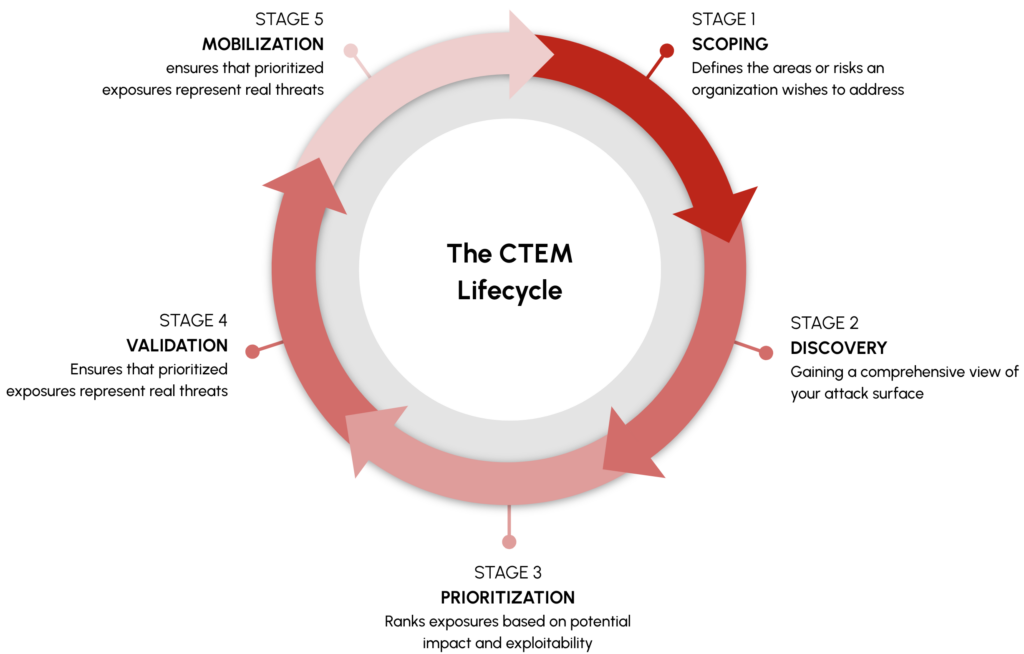
1. Scoping: Know What You’re Protecting
CTEM begins with understanding the complete attack surface. This includes all assets—on-prem, cloud, shadow IT, SaaS applications, and third-party systems. Scoping ensures teams can uncover unmanaged or unknown assets and identify where agents are missing or improperly deployed.
2. Discovery: Move Beyond CVEs
In this phase, organizations identify not only software vulnerabilities, but broader exposures—unprotected identities, misconfigurations, missing controls, and more. This comprehensive and holistic view helps teams focus on what really matters, reducing reliance on narrow CVE-based scanning.
3. Prioritization: Focus on What Matters Most
By layering business context, asset criticality, threat intelligence, and exploitability insights, CTEM enables intelligent prioritization. Instead of chasing every high CVSS score, security teams can focus on the exposures that pose the greatest risks to the business—increasing efficiency, streamlining response, and improving outcomes.
4. Validation: Confirm Exploitability of Exposures
CTEM programs incorporate continuous validation through adversarial simulations, breach and attack testing, and other automated techniques to confirm whether exposures are truly exploitable. This allows security teams to better prioritize their efforts, ensuring they are focusing on the highest-impact risks—those that could realistically be used by attackers to infiltrate the environment.
5. Mobilization: Align Teams and Drive Action
With exposures mapped to specific assets and owners, CTEM makes it easier to orchestrate remediation. Automated workflows, asset tagging, and stakeholder alignment ensure the right issues get to the right teams with clear accountability. Importantly, CTEM incorporates a feedback loop to confirm that remediation efforts have actually resolved the issue—helping teams avoid the trap of “ticket closed” equating to “problem solved.” Continuous monitoring and verification ensure exposures stay closed, not just logged as completed.
Why Technology Is Critical in Supporting CTEM
A successful CTEM program isn’t just a process—it needs the right technology to scale. Given the volume and velocity of assets, vulnerabilities, and exposures in modern environments, manual processes, spreadsheets, and homegrown scripts won’t cut it.
Organizations should invest in:
- Exposure Assessment Platforms to unify data, automate discovery, and support contextual prioritization.
- Adversarial Exposure Validation tools to simulate real-world attack paths and validate remediation effectiveness.
These tools act as the technical backbone of a CTEM program, turning insights into action at enterprise scale.
Conclusion
Traditional vulnerability management is no longer sufficient in the face of today’s evolving cyber threats and expanding attack surfaces. Organizations need to move from reactive patching to proactive exposure reduction.
By adopting a CTEM framework, security leaders can:
- Gain full visibility into their attack surface
- Advance beyond CVEs to assess all types of exposures
- Prioritize efforts based on real-world risk
- Validate that remediations are effective
- Align teams around measurable, continuous improvement
It’s time to rethink how we manage cyber risk—not just by fixing vulnerabilities, but by reducing the exposures that matter most. Welcome to Vulnerability Management 2.0.
