Sevco Security is now part of Arctic Wolf. Read the press release.
One Platform to Power Exposure Management and CTEM Programs
Discover, prioritize,
and resolve risks—
at scale.












3.5B
Asset attributes
processed/day
1.5M
Unique exposures
surfaced in 90 Days
Up to 25%
Assets found with CVEs missing patch agents
28%
Assets found missing
a security control
Mission Control for Security Teams
The Sevco Exposure Assessment Platform
Centralize exposures across your attack surface to proactively reduce critical cyber risk. Manage asset inventory, vulnerability management, cloud security, and remediation with one platform.
See Sevco in action. Take a self-guided tour here.
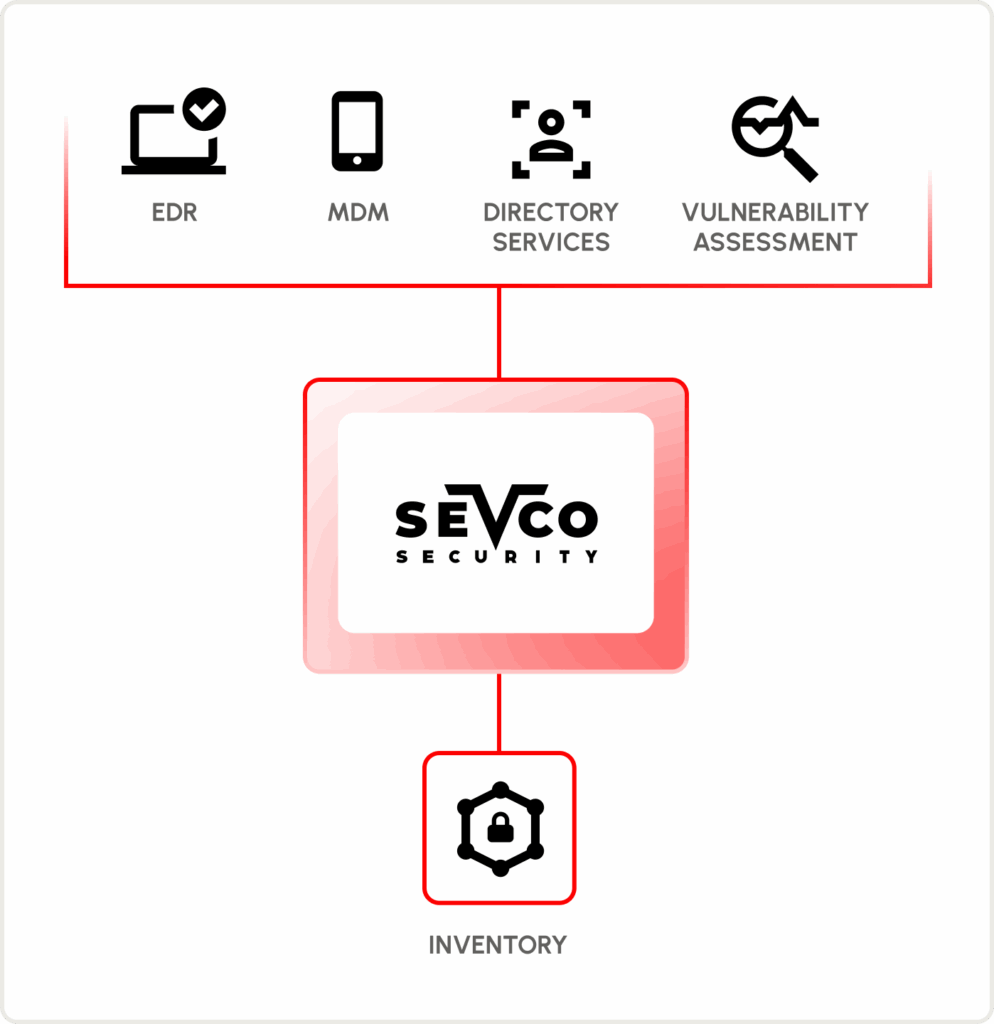
Generate and maintain a live inventory of assets.
Utilize 1000+ integrations to automatically manage a real-time inventory of your devices, identities, software, vulnerabilities, and security controls.

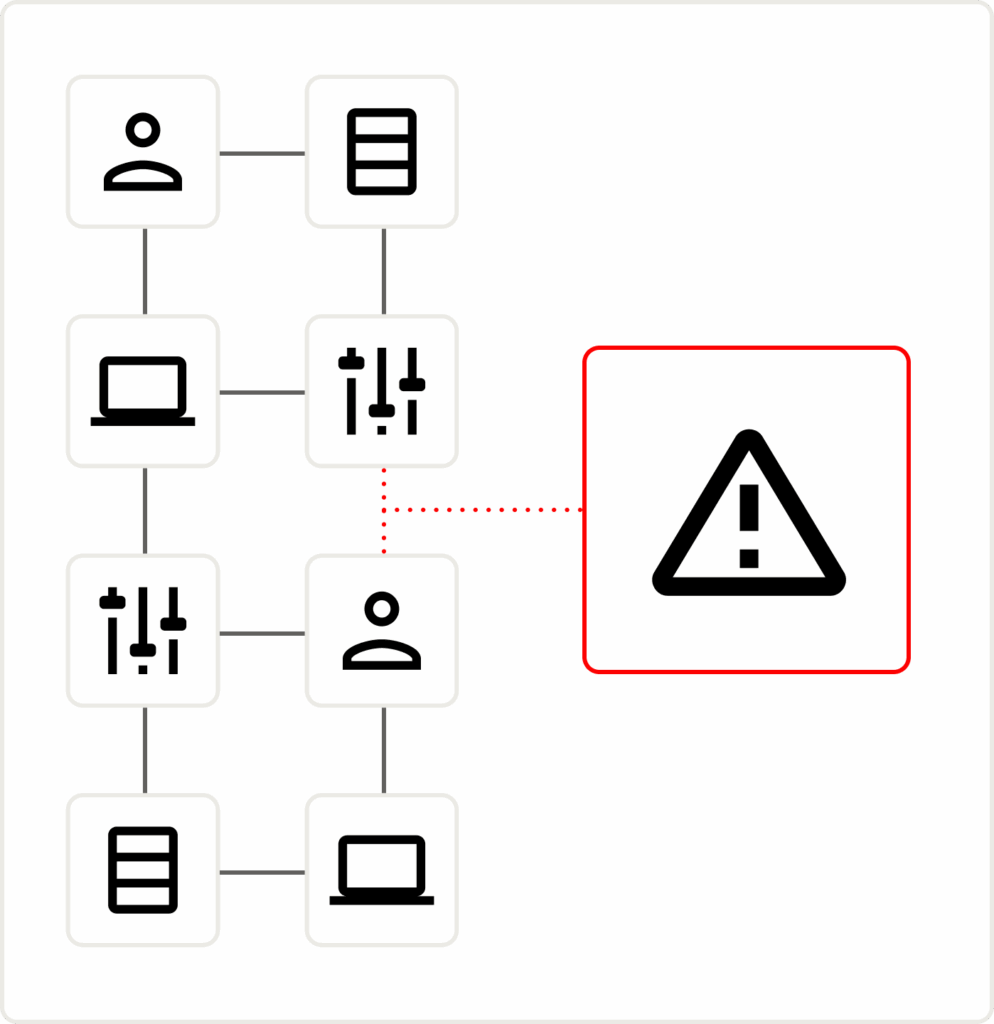
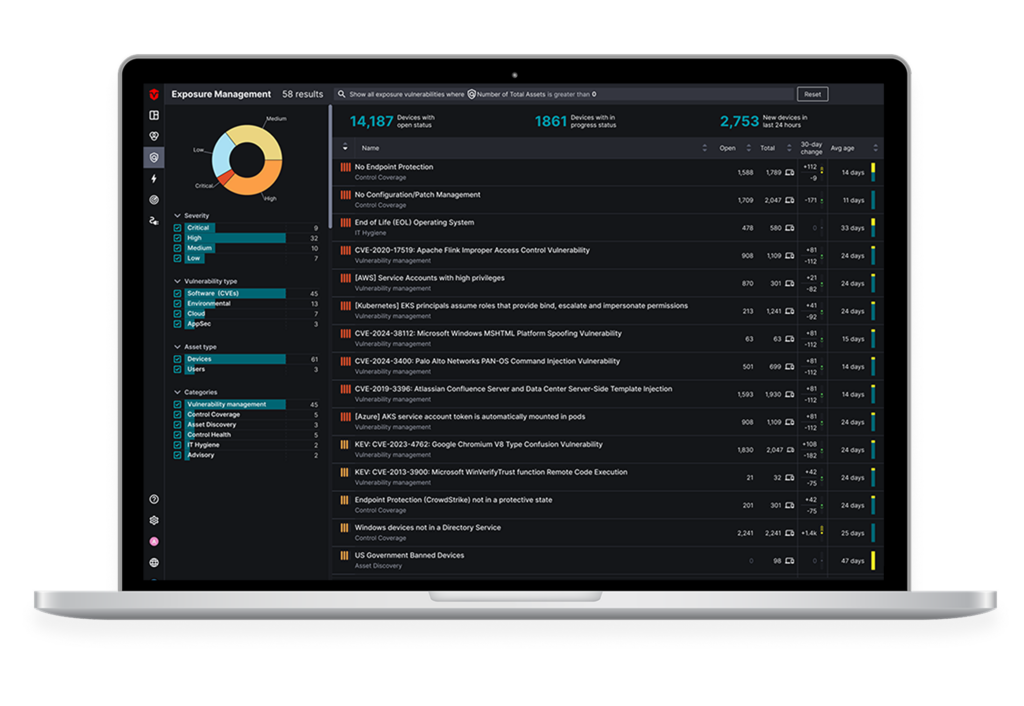
Vulnerability Management 2.0
Discover weak points in your security posture
Monitor the relationships between all vulnerabilities, assets, users, compensating controls, business context, and relevant threat intelligence.

Cloud Security Posture Management
Secure your cloud environments
Reduce risk associated with critical attack paths by consolidating your Cloud Native Application Protection Platform (CNAPP) findings—inventory, misconfigurations, permissioning, vulnerabilities, and more.
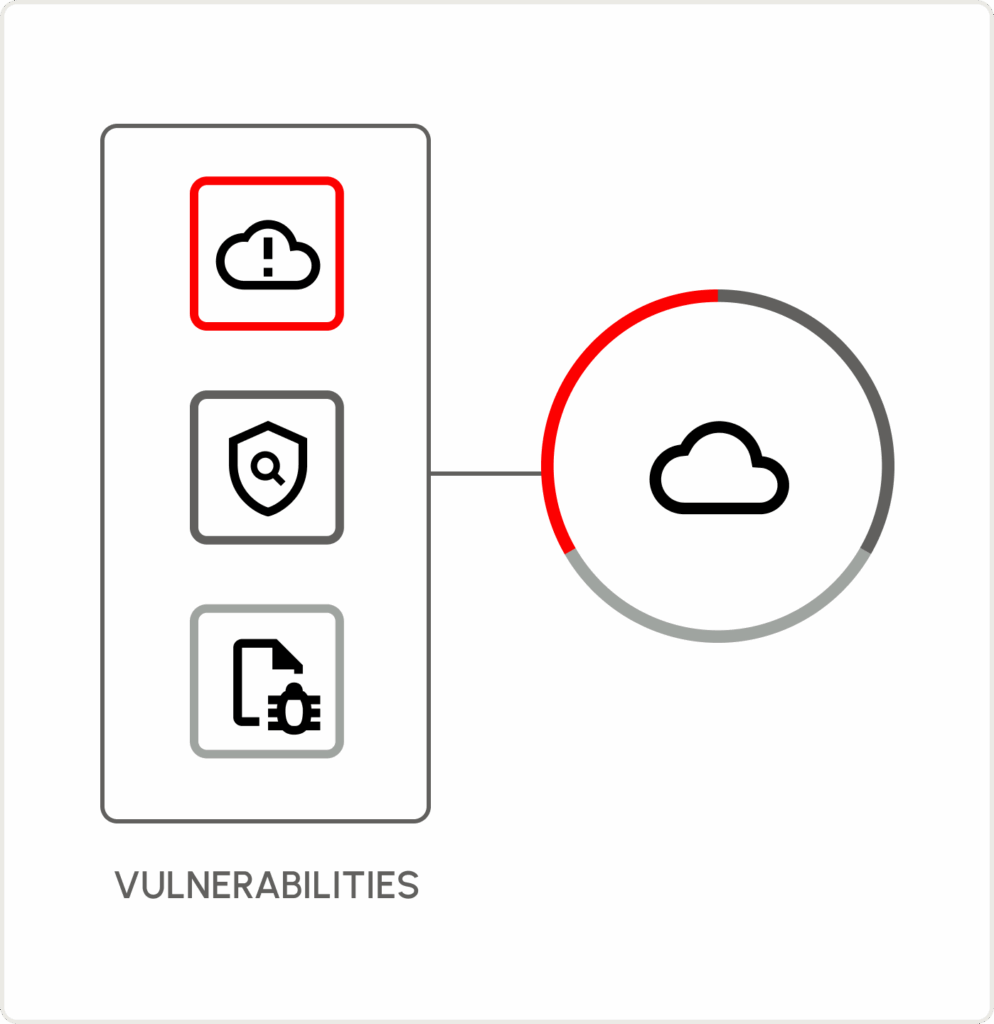

Risk Quantification
Prioritize risk – specific to your business
Leverage the intelligence from across your entire attack surface to quantify risk and rank critical exposures beyond just CVEs.

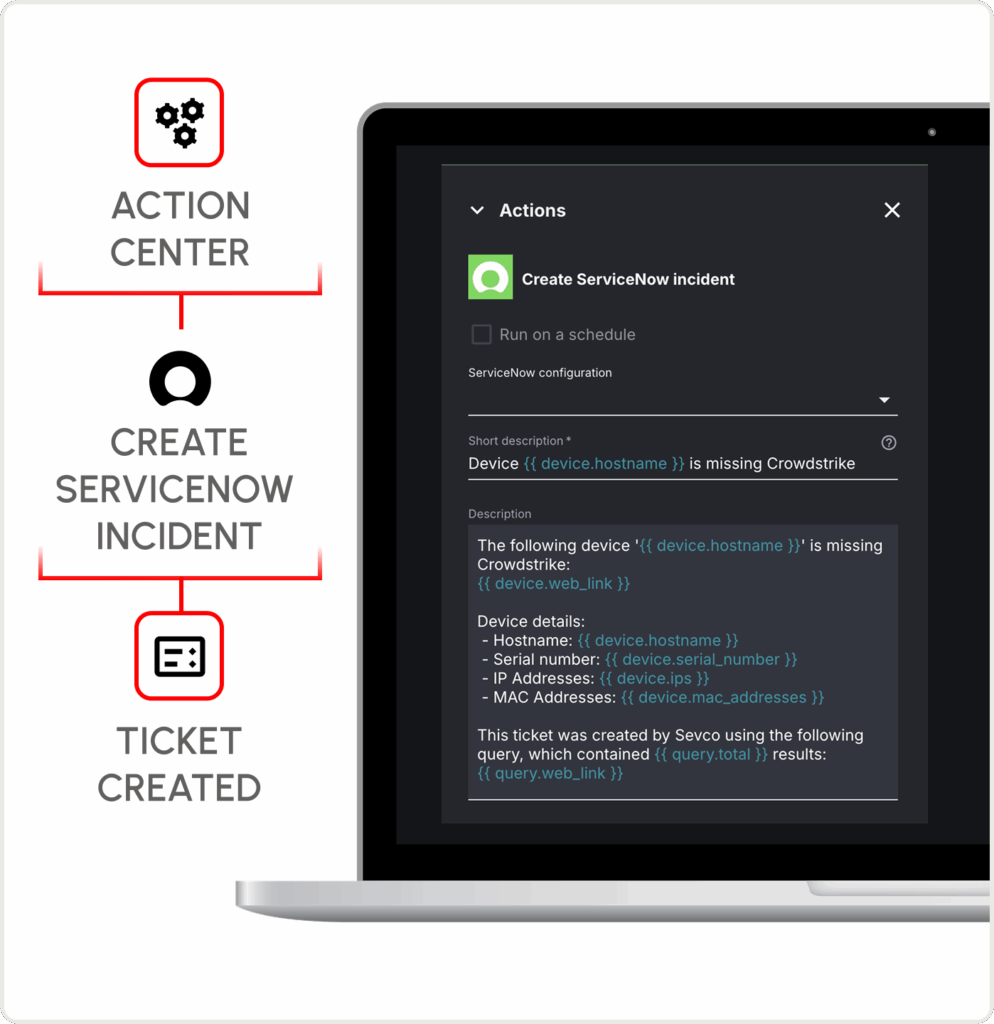
Mobilization & Remediation
Operationalize cross-functional remediation
Take action to burn down cyber risk and report on the health of your Exposure Management program.
Real stories, real results.
See what success looks like with Sevco.
Uplevel your vulnerability management to Continuous Threat Exposure Management (CTEM) with Sevco
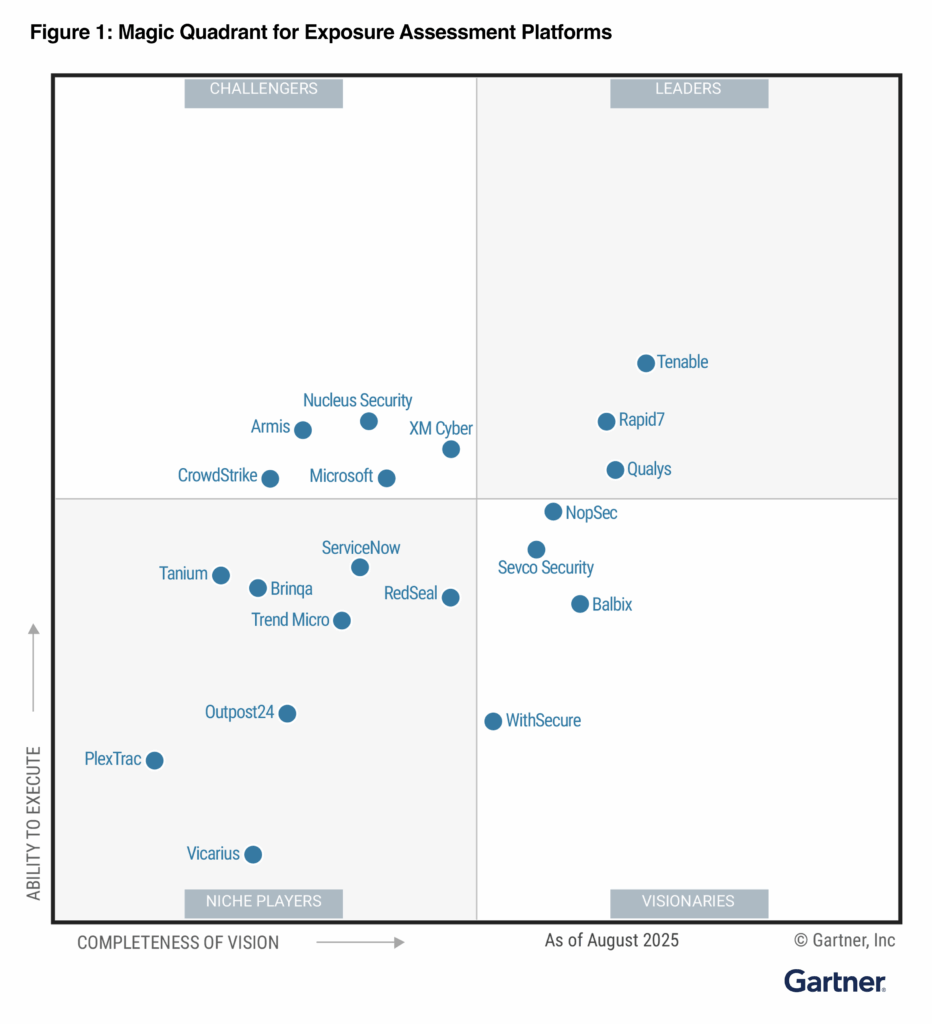
AWARDS
Proud to earn industry trust.














