IT Operations.
The most accurate asset intelligence to manage, optimize, and secure your environment like never before.
Rogue risk.
Don't fear the unknown. Address it.
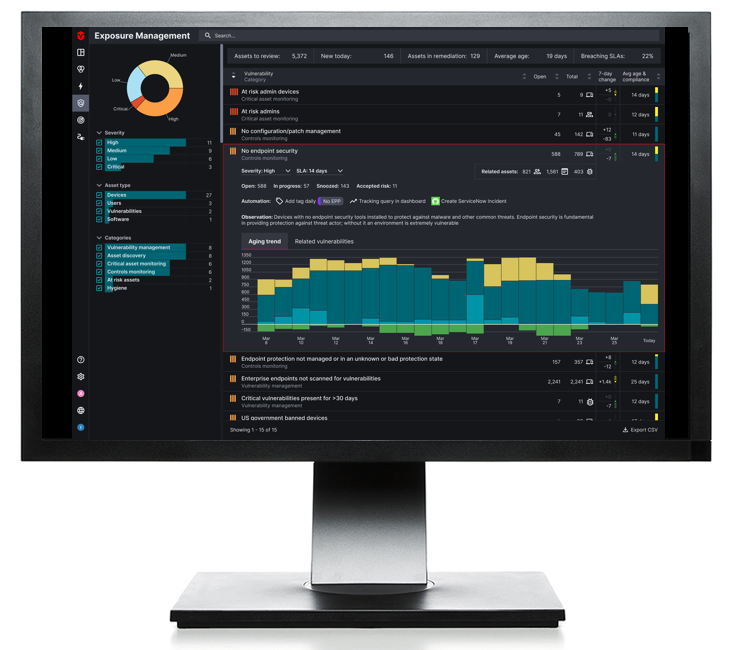
Prevent rogue access
Continuous monitoring and inventory of assets and users to provide real-time visibility to rogue-access.
Fast unauthorized detection
Fast detection of unauthorized assets and users through data-rich dashboards.
Pinpoint rogue devices
Real-time telemetry and enriched asset intelligence for pinpointing rogue devices.
Automated workflows
Automated workflows for efficient IT, security, and operational processes.
Centralized access view
Complete and centralized view of user accounts for swift identification of access privileges that need to be changed.
End-of-life systems.
When they're on their last leg, be sure it doesn't kick you in the pants.

EOL system identification
Quickly identify and prioritize EOL systems for replacement or upgrade.
Downtime risk reduction
Decrease the risk of downtime associated with EOL systems.
Legacy system cost savings
Lower costs associated with legacy system maintenance and support.
Compliance risk mitigation
Reduce compliance risks and avoid potential fines or penalties for unsupported systems.
CMDB reconciliation.
To be a source of trusted information it helps to rely on one.
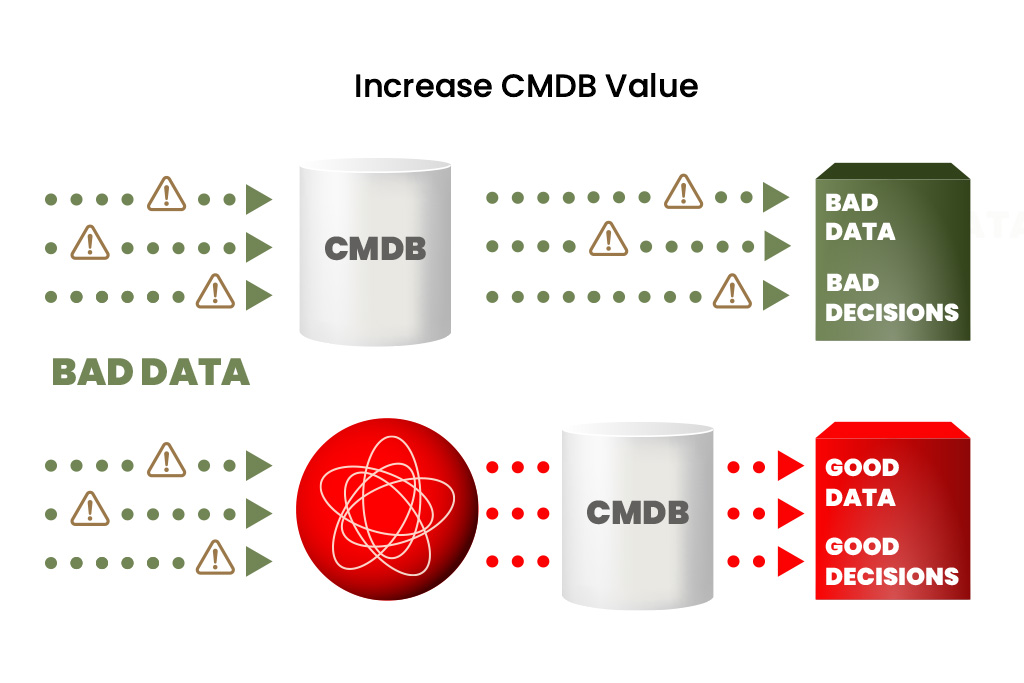
Precise reconciliation process
Implement a more precise and efficient reconciliation process with accurate real-time information.
Informed technology decisions
Make more informed decisions about technology investments, resource allocation, and risk management.
Asset relationship tracking
Track the relationships between different assets to quickly identify the root cause of problems and incidents.
Accurate asset records
Maintain accurate and complete records of IT assets for compliance and audits.
Questions about use cases?
We can answer any questions regarding IT Operations or other related topics. We're passionate about the power of the Sevco platform and eager to share its benefits with you.
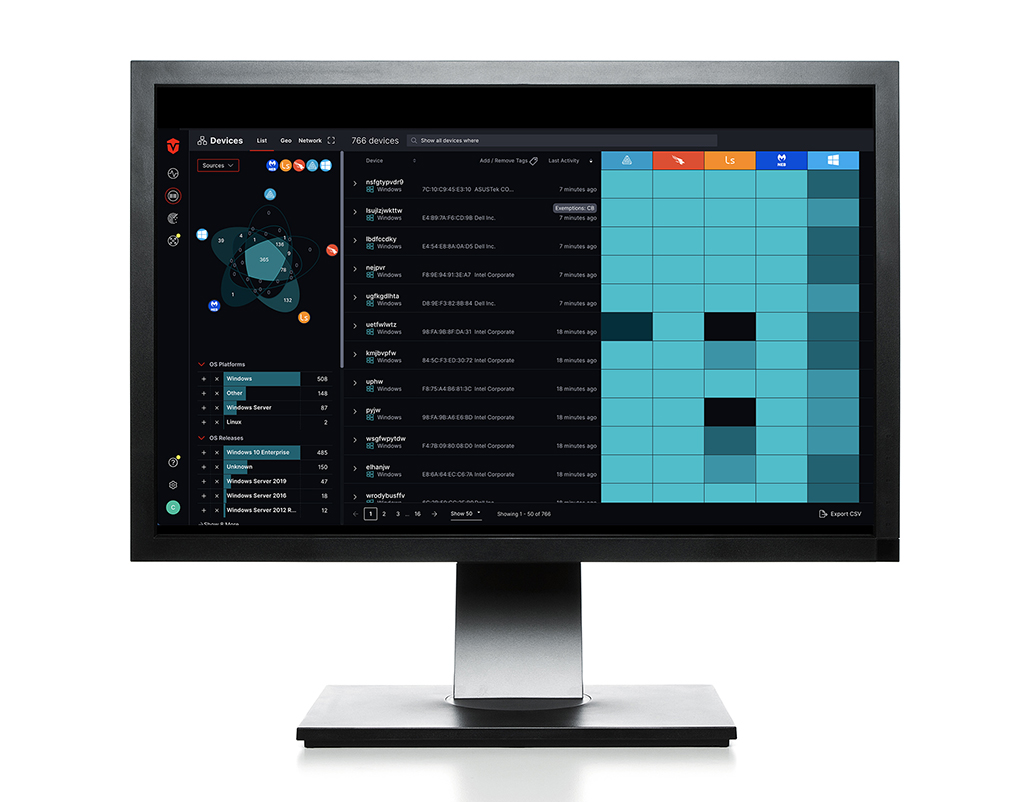
Explore other use cases.
How the Sevco platform helps people in the trenches every day.
What our customers say about us
"Sevco’s value cannot be overestimated, just one missed device can compromise an entire company."
Grigiory Milias, RFA
"Sevco is a high-impact solution that was quick to configure and delivered extremely quick time-to-value. Having a comprehensive understanding of our assets has really helped us to maximize the investments of my existing tools."
Cecil Pineda, R1 RCMChief Information Security Officer
"Visibility into device inventory is foundational to every security program. It’s challenging to ensure that information stays accurate and updated. Sevco quickly delivers this information to the team and gives us the ability to confidently take action and make informed decisions."
Everett Bates, EverviewChief Information Security Officer
“Sevco gives us the ability to help our customers identify gaps that they did not know existed, giving them an accurate picture of their real attack surface. Partnering with Sevco has delivered immediate value, enabling us to scale quickly and deliver important, foundational security services to our customers across the world.”
Jason Norred, Solutions IIChief Information Security Officer
"Every time I go into Sevco, I find something cool. The improvements you guys are constantly making is impressive. We use this more than some other tools - we still need those other tools, but you all bring it into one place."
Aaronisa Barnes, Quality CarriersSecurity Administrator
The latest in asset intelligence.

Here are the top five reasons why an EAP is the key enabler for service providers to deliver CTEM programs quickly and efficiently.

We believe our position validates our vision is the right one for the future of cybersecurity. We are building the system of record for cybersecurity.

Find vulnerabilities. Patch vulnerabilities. Repeat. Sound familiar? What worked just over 5 years ago is no longer sufficient today.

Now that October 14, 2025 has come and gone, Windows 10 EOL devices may be leaving you more vulnerable than you think.

Traditional vuln management was built for a different era – it wasn’t designed for today’s environments. Learn why exposure management is.

Security teams must evolve past basic device discovery to identify device authority—determining which endpoints truly fall under corporate control..
Take the next step in securing your assets today
Schedule a one-on-one platform walkthrough to see what Sevco can do for you.
AWARDS
Proud to earn industry trust.
















