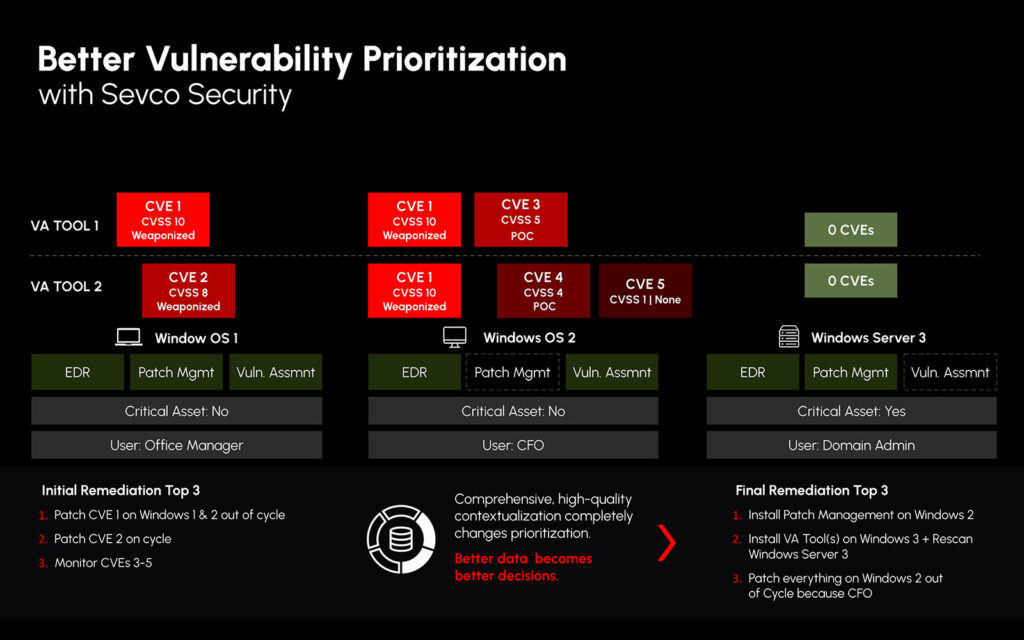
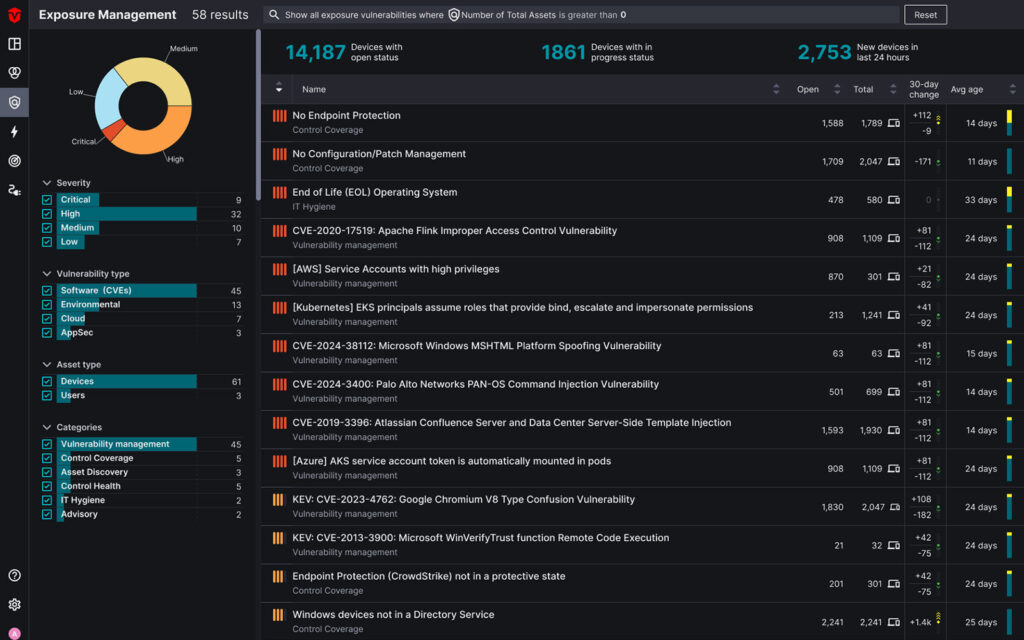
The Future of Vulnerability Management: Exposure Management
Legacy vulnerability programs aren’t designed for today’s hybrid workforces, sprawling cloud infrastructure, or modern attackers. That’s why there’s a shift towards Exposure Management.
The Future of Vulnerability Management: Exposure Management Read More »