Prioritize the Vulnerabilities That Actually Matter.
Full visibility and control over cyber assets
enables better decisions.

How Sevco’s RBVM Helps Security Teams
Unify your vulnerability data with asset inventory, threat intelligence, and business context for holistic risk-based vulnerability prioritization. Focus on remediating real risk that stops breaches instead of burning down a backlog.

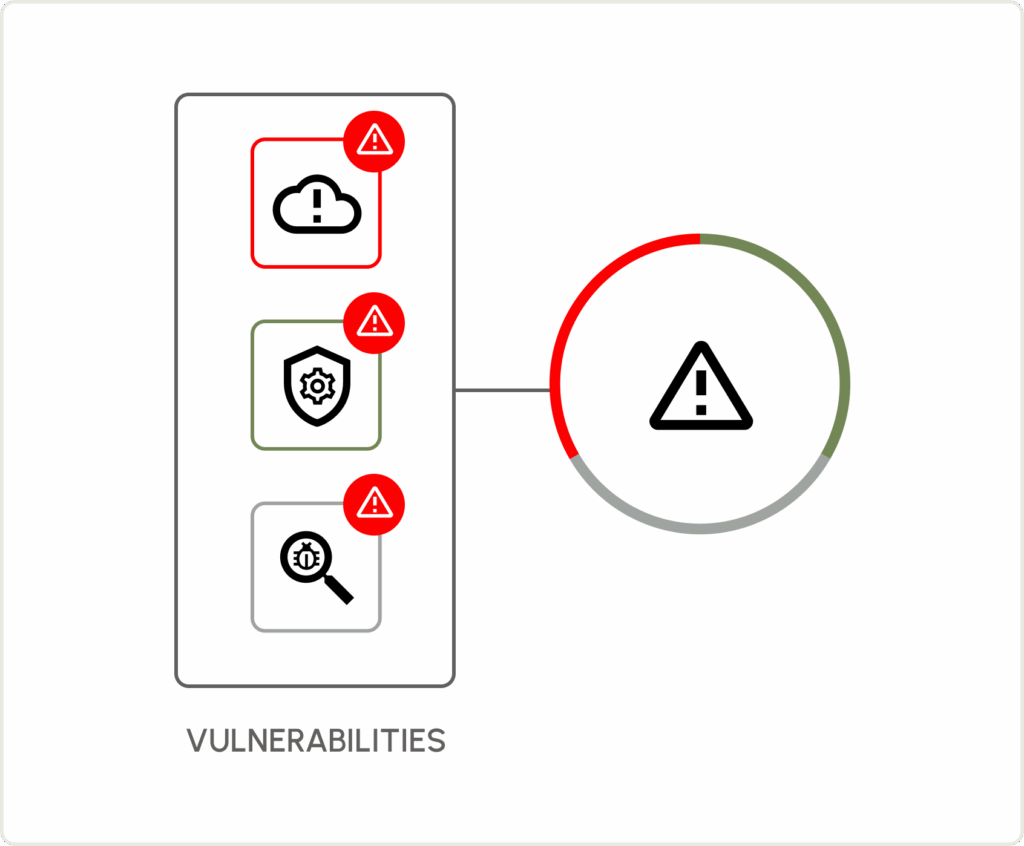
Consolidated Vulnerabilities.
Take an asset inventory approach to vulnerability management. Integrate with all of your vulnerability sources to discover the full scope of your vulnerabilities and uncover hidden risks.
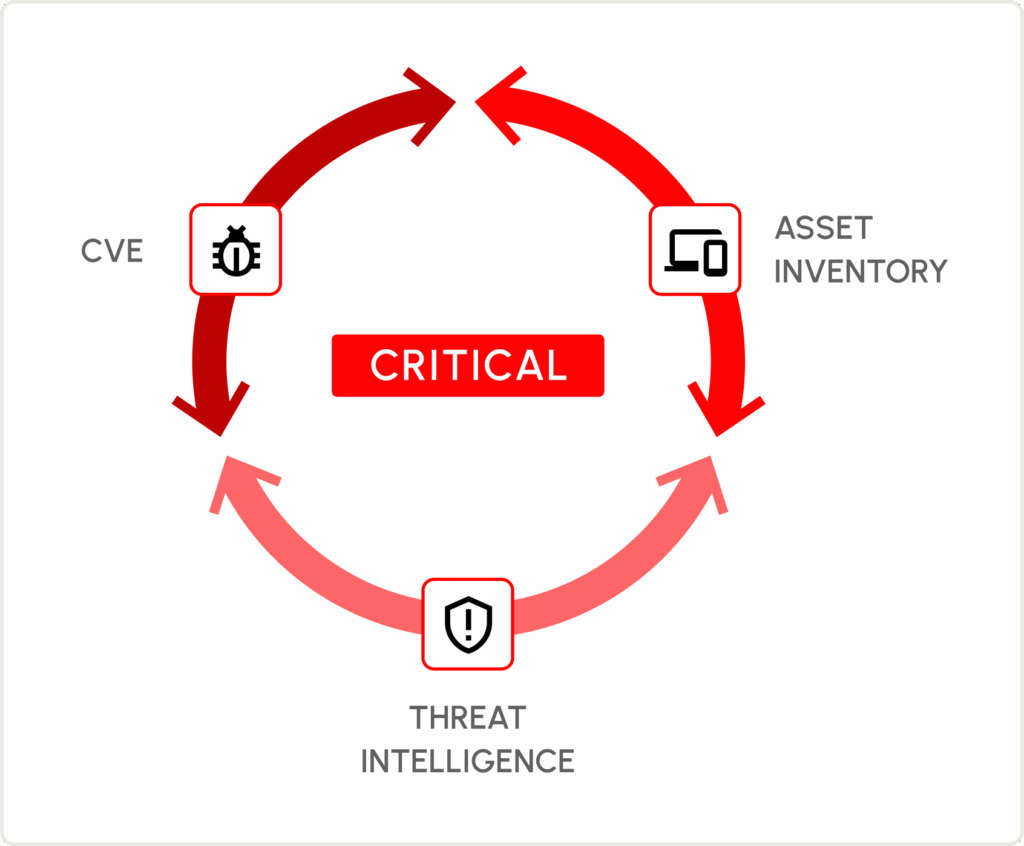
Native Intelligence.
Automatically correlate active threats and relevant data from Sevco’s vulnerability intelligence, CISA KEV, and EPSS to all of your vulnerabilities for improved prioritization.
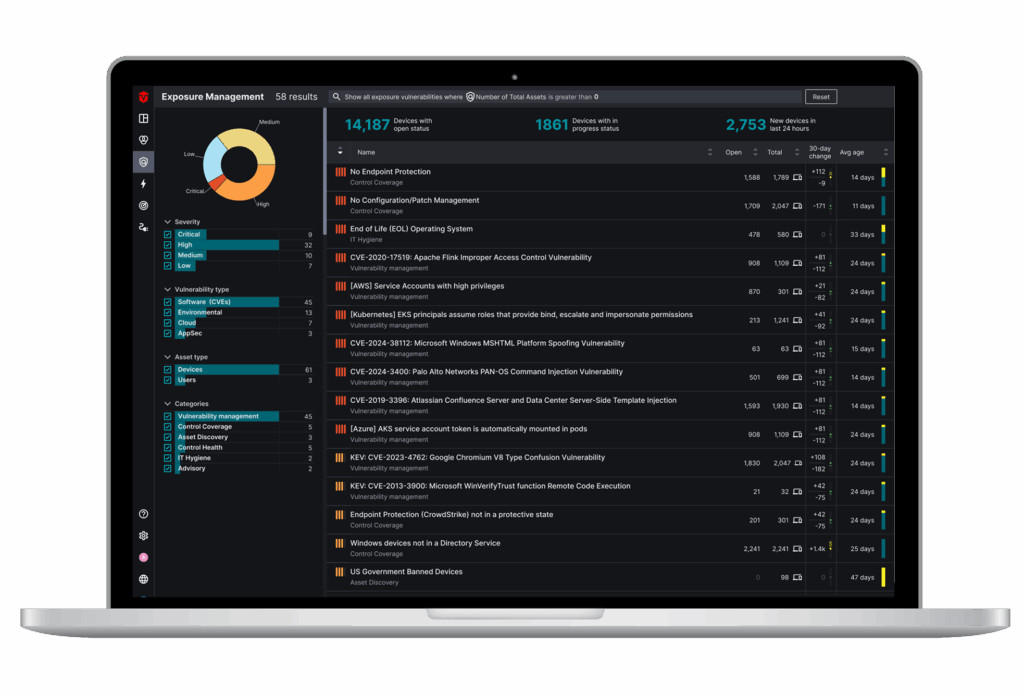
Custom Prioritization.
Combine Sevco’s context around vulnerabilities, assets, threats, and business context to create prioritization frameworks specific to your needs. Or, utilize out of the box risk scoring to take action against critical vulnerabilities.
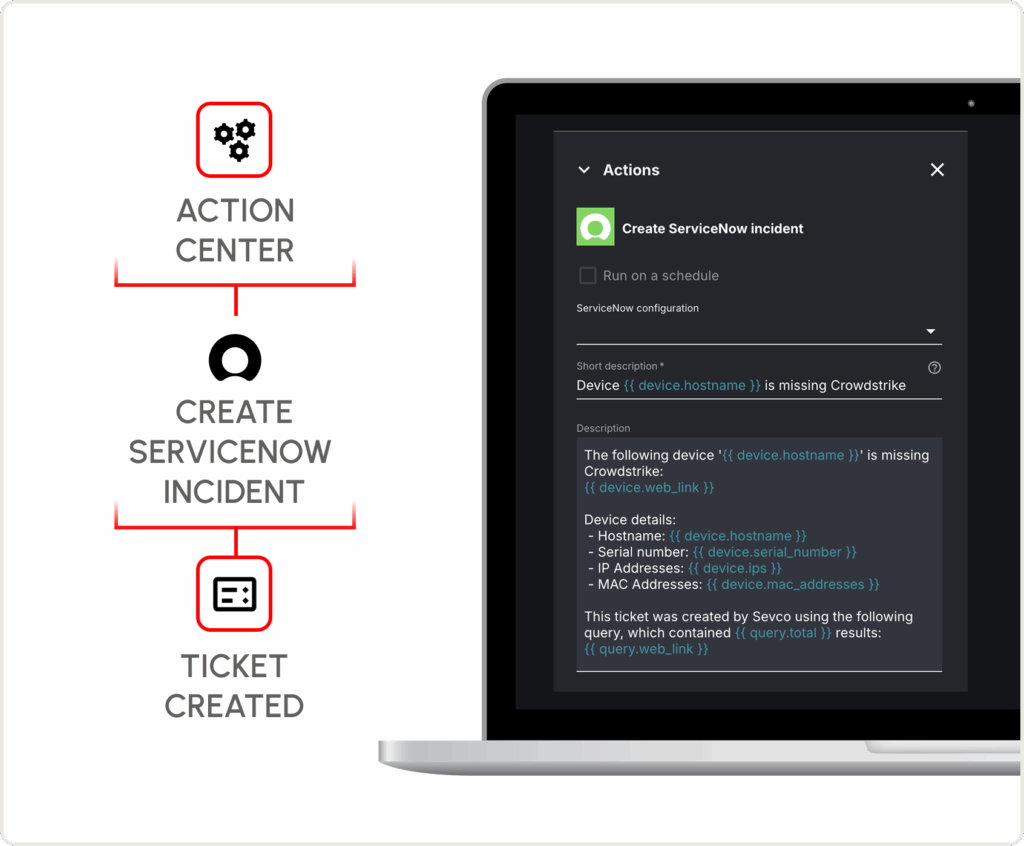
Automated Actions.
Set custom rules, triggers, tickets, notifications, and outbound integrations that automate your remediation and patch workflows. Sevco’s platform continuously monitors for changes to ensure that risks are resolved—regardless if a ticket is closed.
How is Sevco different?
All Vulnerabilities
Ingest, normalize, and deduplicate data from all of your vulnerability sources for the full picture of risk—go beyond a siloed report from a single vendor.
Asset Correlation
Prioritization requires context. Utilize application, device, user, and vulnerability data together to radically improve your approach to ranking risk.
Relevant Intelligence
Leverage severity, exploitability, asset inventory, business context, threat intelligence, and external data to prioritize vulnerabilities that matter to your organization.

ASSET
Modernize Your Vulnerability Management
A shift in strategy is needed to move past traditional vulnerability management—one that incorporates a holistic view of the attack surface, automates prioritization, and applies business context to every decision. Learn the strategies to move to a proactive and holistic approach to reduce risk in this whitepaper.
Key RBVM Features
Vulnerability Inventory
Unifying, normalizing, and deduplicating vulnerabilities from all of your sources— automatically.
Asset Graph
Mapping the relationships between applications, devices, users, and vulnerabilities to optimize prioritization.
Risk Quantification
Scoring your vulnerabilities on the dimensions of severity, exploitability, and business impact.
Real stories, real results.
See what success looks like with Sevco.
Take your vulnerability managment to the next level.
AWARDS
Proud to earn industry trust.














