The Criticality of a Security Asset Inventory
The concept of Cyber Asset Attack Surface Management (CAASM) was introduced several years ago and brought together cyber asset management and vulnerability analysis. But to truly reduce risk, organizations need to move beyond simply looking at their cyber assets and CVEs. Enter Exposure Assessment Platforms – or EAPs. The most effective EAPs are built on the foundation of CAASM, but also include vulnerability assessment, vulnerability prioritization, and threat intelligence. An EAP provides comprehensive data on devices, identities, applications, users and vulnerabilities—in addition to business context to help security teams prioritize risks and exposures as they relate to their specific operations.
In the past, security teams have often relied on an “IT asset inventory”. However, the inventory needs of an IT team and a security team are vastly different. Where an IT asset inventory can be “good enough” to still serve its IT function, what security teams need is a true system of record that includes devices, identities, applications, users, and vulnerabilities—that’s up-to-date in real time.
A security asset inventory needs to be comprehensive and remain current, allowing you to continually verify that your security coverage remains complete in a dynamic environment where change is constant. The importance of implementing a sound security asset inventory strategy cannot be overstated. For this reason, a security asset inventory is a foundational security control that is prominently featured in nearly every security framework such as the CIS Critical Security Controls and NIST Cybersecurity Framework. A security asset inventory is the foundation upon which your security architecture is built, providing the essential groundwork for your organization’s effective defense.
There are plenty of options when it comes to achieving this level of sophistication. We’ll explore various security asset inventory strategies, offering a look at the pros and cons of each approach.
Mind the security gap
Are you confident that you have a complete view of your asset inventory? The answer in most instances is no. But what’s causing gaps in your asset inventory?
- Relying solely on one source for your inventory. When you’re only pulling data from a single tool and not aggregating inventory from multiple tools, you’re missing out on the complete picture. This often leaves assets without proper security coverage.
- Aggregating inventory is not for the faint of heart. For those attempting to aggregate inventory from multiple sources, you know the struggle all too well. It takes expertise, an inordinate amount of time, and a deep understanding of different tools to sort through and deduplicate IT inventory feeds.
- Overlooking details on the state of your assets. A typical IT inventory only reports the presence of an asset (e.g., it exists), neglecting details on its state (e.g., it’s up or it’s connected). Understanding the asset state is crucial because it provides details such as the configuration state or whether the asset is checking in appropriately with the security tool to receive updates.
Essential requirements for your security asset inventory strategy
A CISO is accountable for the security of the organization, which foundationally lies on an inventory of assets. But relying on the IT team’s asset inventory isn’t accurate (enough). There’s no driver for IT to do any better because they’re not accountable for inaccuracies and mitigating risk, which puts security in a difficult position. A security asset inventory enables security to take control of their own destiny.
Aggregation: Getting a complete inventory
- It’s crucial to aggregate data from various tools to paint a comprehensive picture of your inventory. After all, each tool offers a different perspective of your environment.
- In an ideal scenario, aggregation goes beyond simply identifying the presence of an asset. It also delves into its state. For instance, knowing if a Windows client hasn’t checked into your EDR solution in days, but checked into your patch management an hour ago could signal potential security risks.
- Do your tools capture change events for each device and how frequently? An optimal solution will consistently gather and keep a thorough history of change events, which will serve as an invaluable aide in your troubleshooting and incident response investigations.
Cross-referenced analysis: Ensuring the inventory is accurate
- Accurate cross-referenced analysis (also called correlation) between assets across tools is essential to identify which ones are the same device. This process involves consolidating, reconciling, and deduplicating multiple sources of asset information to determine the true unified view of your inventory.
- Correlation can be deceivingly complex where inaccurate analysis can result in duplicates (i.e., the same asset getting included twice), leading to unnecessary remediation efforts. Conversely, inadvertently merging several devices into one can create serious gaps in your security coverage.
Ease of management: Simplifying and scaling the process
- Keeping up with an ever changing IT landscape is challenging, to say the least. Your inventory approach needs to be as nimble as your organization, ensuring you can seamlessly incorporate new data sources as your business grows.
- When it comes to keeping your security coverage at optimal effectiveness, you can’t have a stale view of your asset inventory—a point-in-time snapshot of your environment might be leaving you exposed.
Security asset inventory approaches
We have uncovered five unique approaches that organizations can adopt, each offering different levels of effectiveness.
Single-source asset inventory
When it comes to IT asset inventory, the objective is clear: obtain a comprehensive list of all assets and consolidate it in one central location. Opting for a single source—like your endpoint management tool—is certainly the easiest route, but it’s akin to putting all your eggs in one basket. Ultimately, if your aim is to identify and close security gaps, this approach falls short of being a viable solution.
Pros
None
Cons
This approach simply doesn’t address coverage gaps.
Relying solely on a single source for asset data is simple, but you’ll have a very limited view of your environment.
Aggregation and cross-referenced analysis are poor: Without aggregating or correlating assets from across tools, this approach is certain to render an incomplete and accurate view of your IT asset environment—only providing what’s visible from a single tool.
Ease is good: While this approach isn’t truly viable for security operations, it’s undeniably the most lightweight option.

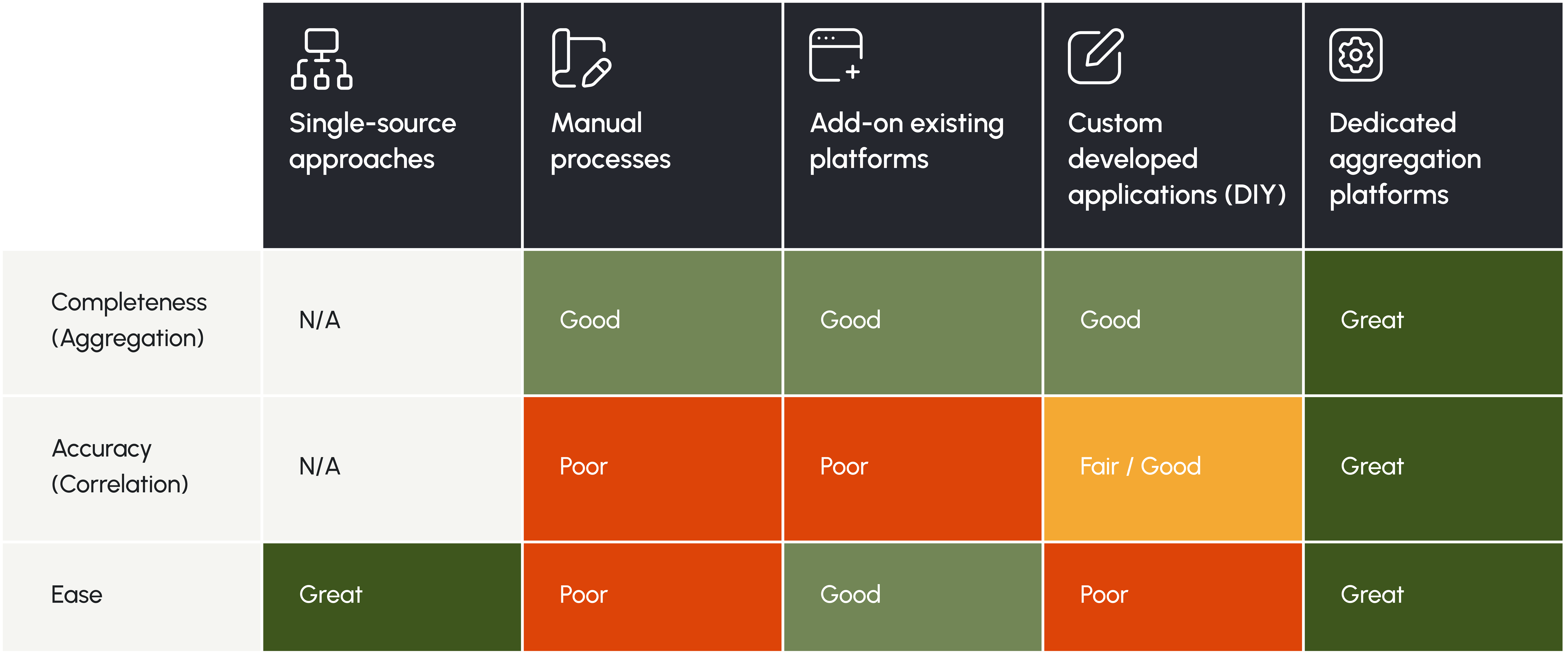
Manual asset inventory process
Another strategy is to manually collect asset inventories from your numerous (siloed) tools and then (again, manually) correlate this data in spreadsheets to create a comprehensive inventory. This list is intended to identify any gaps in tool coverage at the time of its creation.
Research shows that this manual inventory process can take anywhere from 40 to 80 hours to complete². And because of the fluid and dynamic nature of IT environments, by the time you’ve finished compiling the data, your asset inventory is already stale and out-of-date.
Another consideration is that this method is not a proactive approach for managing your security coverage. You will constantly be chasing security gaps because you won’t spot them until after the lengthy process is completed.
Pros
No technical investment needed
Cons
- Like any manual process, undetected errors can result (and may differ from one export of data to the next).
- Tracking assets manually can be a time-consuming endeavor, accounting for up to a full week of precious time.
- While you’ll determine the presence of an asset, you won’t have insights into its current state so identifying potential security issues can become difficult.
- Without automated alerts, it becomes challenging to stay ahead of new security gaps, leaving blind spots.
Aggregation is good (but not optimal): While aggregating data from across tools is the desired method to achieve a comprehensive asset inventory, keeping it current presents a significant complication. Often, organizations that adopt this manual asset inventory process can only update it monthly or quarterly, which falls short of the frequency needed for effective security coverage.
Cross-referenced analysis is poor: Manual correlation introduces inconsistencies and errors, particularly when dealing with a large number of tools and assets.
Ease is poor: Pulling together manual inventories from multiple sources is challenging, especially with any meaningful frequency, as it requires coordination with those responsible for each tool every time they are needed to export the inventory. This adds overhead for them each time the request is made. Also, scalability is an issue: as the complexity of your organization increases, so does the time and resources required for manually managing your inventory spreadsheets.
Add-on module to existing platform
Many platforms boast extra modules designed to pinpoint your IT assets and compile an inventory. These modules provide a bit of convenience, but often veer away from the platform’s main strengths. While they may meet some basic functionality requirements, they usually miss the mark when it comes to validating complete security coverage and identifying gaps, especially when compared to a dedicated solution for asset intelligence.
Pros
Easy extension of an existing platform: You can leverage the familiarity and trust associated with your incumbent vendor.
Cons
Add-on modules often show a correlation bias toward the vendor’s core technology platform. There’s typically a primary source of truth (their platform), and then context is layered on from other sources. This still presents an inaccurate and biased view, especially when compared to a completely impartial asset intelligence solution that doesn’t favor any single tool.
As a result, you’ll likely find yourself needing to perform manual verification to ensure accurate correlation, which demands detailed analysis and manual overrides to correct errors.
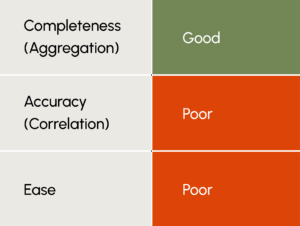
Aggregation is typically good: While this approach may provide a comprehensive asset inventory, it often falls short in capturing the state of assets within tools. Obtaining accurate state information from each tool proves challenging due to the complexities involved in collecting, processing, and correlating disparate data sources.
Cross-referenced analysis is poor: Accuracy suffers due to the inherent bias toward the core platform and the challenges these platforms typically have with achieving accurate correlation. These solutions don’t typically have the same level of comprehensive correlation as they do for the functionality of their core product.
Ease is good: This strategy is generally easy to implement as add-ons to an existing tool; however, your mileage may vary in terms of ease of management and the actionable insights you can get from the information. Also, the scalability and ability to address additional use cases beyond IT asset management may be limited, depending on the architecture and functionality.
Custom developed apps—the “DIY” approach
Another strategy for managing asset inventory involves harnessing internal resources to construct an in-house solution. For security teams keen on taking ownership of mitigating the risk of unprotected devices, developing a bespoke asset inventory solution may seem like the most straightforward path.
However, taking this approach requires lobbying for significant resources. And you’ll need to develop the expertise to navigate the depth, scope, and nuance of collecting and correlating the vast amounts of data across multiple systems—learning the ins and outs to develop a usable tool from scratch. Likewise, you’ll also need to plan for ongoing resources to manage and maintain the solution.
Pros
Your solution is crafted specifically for the systems within your environment and tailored to your unique requirements and preferences.
.
Cons
- This approach typically lacks the in-depth expertise required for robust correlation analysis, potentially leaving blind spots in your security coverage.
- In-house solutions are often less effective with incomplete, inaccurate, and stale data, compared with best-of-breed solutions built on best practices gleaned from diverse IT environments.
- Be prepared to allocate resources (in both time and expense) for maintaining the solution over time.
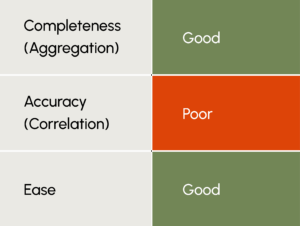
Aggregation is good: With a custom-designed solution tailored to integrate seamlessly with all of your sources, you’ll achieve a comprehensive view of your asset inventory, particularly in terms of asset presence. However, gaining insights into asset state presents a different challenge, as it requires navigating the complexities of collecting, processing, and correlating disparate source data.
Cross-referenced analysis is fair to good: The accuracy of cross-referenced analysis hinges on the expertise your team has dedicated to building a robust correlation engine capable of accurately deduplicating assets.
Ease is poor: This approach demands significant overhead, relying heavily on the time and effort of your in-house engineers for both development and maintenance. Additionally, keeping up with constantly evolving APIs means having to stay on top of regular updates, which adds to the workload and cost. Scalability poses another hurdle as scaling for data consolidation, analysis, and de-duplication can prove challenging.
Dedicated aggregation platforms
Cyber Asset Attack Surface Management (CAASM) platforms seamlessly integrate with your existing security tools, automating the aggregation, correlation, and deduplication of your asset data. Leading solutions offer features such as queries, automated alerts, and integrations with ticketing systems to expedite remediation. By consolidating deep asset data from across the enterprise toolset into a single pane of glass, these platforms also support broader security use cases—prioritizing vulnerabilities, navigating incident response investigations, and ensuring compliance.
Pros
- Expertise in aggregation and correlation pipelines, ensuring your asset intelligence data is complete and accurate.
- You’ll benefit from the vendor’s expertise and resources dedicated to managing and maintaining the platform and its integrations. This support is particularly valuable as APIs tend to undergo frequent changes.
- Dedicated platforms typically provide numerous features tailored specifically to address security gaps, meet compliance mandates, and more.
Cons
These will be new additions to your tech stack, which require onboarding and deployment.
Aggregation is great: Dedicated solutions offer in-depth insights into devices, identities, applications, users and vulnerabilities within your environment. The most modern solutions provide a real-time, comprehensive security asset inventory that include detailed information on both the presence and state of each asset, ensuring you have a thorough understanding of your IT environment and can swiftly surface any gaps in security coverage.
Cross-referenced analysis is great: Opting for a dedicated platform ensures top-tier normalization and deduplication providing an accurate, unified view of your inventory that’s continuously updated—no more relying on outdated data.
Ease is great: These solutions are designed to provide a seamless user experience. Implementation is simple and straight forward, only requiring only the one-time set up of the API connections. The need to ask tool owners for their tool’s inventory data disappears. Dedicated platforms seamlessly integrate into your existing remediation workflows, making your security processes even more efficient and effective. And these cloud-native dedicated solutions are scalable, easily adapt to growing environments.

The Sevco Exposure Assessment Platform
With Cyber Asset Attack Surface Management (CAASM) as its foundation, the Sevco platform has evolved to include vulnerability assessment, vulnerability prioritization, and threat intelligence—to become a true Exposure Assessment Platform (EAP) that provides comprehensive data on devices, identities, applications, users, and vulnerabilities and the relationships between them.
The Sevco Exposure Assessment Platform enables you to:
- Scope your attack surface and discover all of your assets
- Identify high risk exposures associated with your assets and correlate them with threat intelligence and business context
- Take a truly risk-based approach to vulnerability prioritization to reduce risk, rather than chase endless alerts
- Verify exposures are efficiently remediated
With Sevco, you can centralize exposures across your attack surface to proactively reduce critical cyber risk. Manage asset inventory, vulnerability management, cloud security, and remediation with the Sevco Exposure Assessment Platform.
Trust Sevco to become the system of record for your security program. Schedule a demo today.
