When Microsoft announced that Windows 10 support would end on October 14, 2025, most security teams filed it away as another deprecation timeline to manage. After all, we’ve been through this before with Windows 7, Windows XP, and every other version. Organizations budget for replacements, plan migration waves, and eventually get it done.
But the data we’re seeing across Sevco deployments suggests something different is happening this time—something that could leave significantly more organizations vulnerable than anyone expected.
The Real Numbers Behind Windows 10 Exposure
Let’s start with the uncomfortable truth, this a lot more widespread problem than most think:
- 79% of organizations we monitor still have Windows 10 systems in production.
- These systems represent 11% of all devices across our customer base.
- Even more concerning, 76% of organizations have Windows 10 systems categorized as Enterprise Endpoints meaning these aren’t just forgotten devices in a closet somewhere. They’re managed workstations that organizations believe are part of their secured infrastructure.
- These systems make up 28% of all Enterprise Endpoint Desktops (Enterprise Endpoints with Windows or macOS operating systems).
One of the ways Sevco Security tracks these types of systems for our customers is our End-of-Life (EOL) Systems dashboard and these insights allow us to see the prevalence of Windows 10 and other EOL operating systems across our customers.
[Note: We use the term End-of-LIfe (EOL) in this blog post but recognize that Microsoft uses Mainstream Support, Extended Support and Beyond Extended Support as well as Extended Security Updates in their Fixed Lifecycle Policy (https://learn.microsoft.com/en-us/lifecycle/policies/fixed). EOL is used here for simplicity and to align more broadly across vendors.]
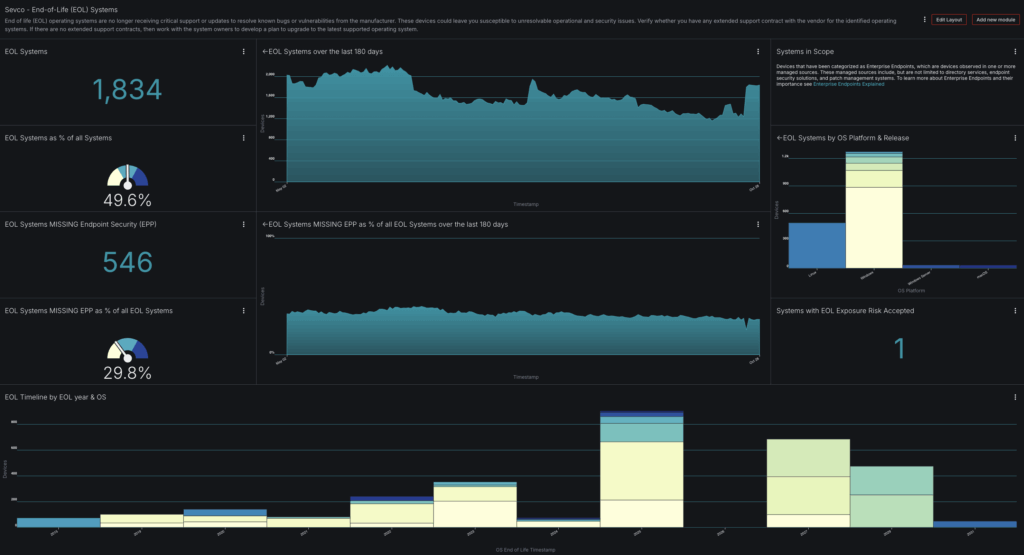
This dashboard shows a typical enterprise picture: 1,834 EOL systems representing 35% of all systems. But here’s where it gets interesting: 546 of these systems are missing endpoint protection entirely, despite being categorized as Enterprise Endpoints that should be protected. Tracking these types of insights is useful for managing the OS lifecycle of systems generally.
Let’s dig into 5 questions organizations should ask themselves around Windows 10 EOL specifically, and what you can do about them.
Question #1: Do We Know How Many Windows 10 Systems We Have?
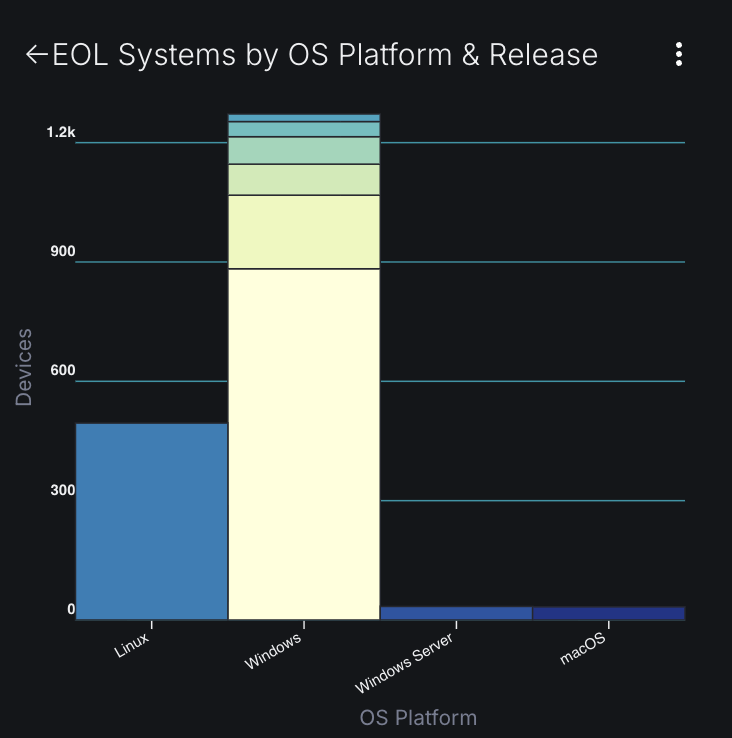
The first technical challenge security teams face is understanding what they actually have. Look at the “EOL Systems by OS Platform & Release” chart in the dashboard. You see distinct counts for Linux, Windows 7, Windows Server, and macOS—but within each category, how do you know you are counting everything? How do you know you’re not double-counting?
The Reality
Most organizations don’t have an accurate, up-to-date view of what they have in their environment. Most organizations will need to pull device inventory from 5-10 different sources to build an accurate state of inventory:
- Active Directory and Azure AD
- Endpoint security agents (CrowdStrike, Microsoft Defender, SentinelOne)
- Mobile Device Management (Intune, JAMF)
- CMDB (ServiceNow)
- Network access control systems
- SIEM correlation logs
- Vulnerability scanners
Each source reports devices differently. Active Directory uses hostname or SID. CrowdStrike uses Agent ID. Intune uses Azure AD Device ID. Vulnerability scanners use IP addresses, which change for laptops moving between office, home, and other remote work locations.
The Solution
First, implement proper device correlation. You need a system that can match devices across sources using multiple attributes:
- Exact hostname matches
- Serial number correlation
- MAC address matching (accounting for virtual interfaces)
- Domain account associations
- Cloud instance ID matching
This isn’t a simple database join. Windows 10 laptops might show up as:
- LAPTOP-USER123 in AD
- laptop-user123.domain.com in DNS
- Serial number 5CD1234ABC in ServiceNow
- Agent ID abc123-def456-ghi789 in EDR
Build lookup tables that normalize hostnames (strip domain suffixes, standardize case, handle machine account suffixes) and MAC address (normalize to one of dash, dot, or colon delimited).
Create confidence scoring—a device matching on serial number + hostname is most likely the same device. A device matching only on IP address that changed two weeks ago is probably not.
Question #2: Do We Have An Extended Support Strategy That Makes Sense?
Microsoft offers Extended Security Updates (ESU) for Windows 10, and many organizations will buy themselves an extra year or three. Problem solved, right?
The Reality
ESU is not the same as standard support. Understanding what you’re actually getting requires reading the fine print:
- Only security updates: No feature updates, driver updates, or non-security bugfixes
- No application compatibility testing: Third-party vendors won’t test against ESU systems
- Increasing cost: ESU pricing increases each year (Year 1: $61/device, Year 2: $122, Year 3: $244 for Enterprise)
- Deployment complexity: ESU requires MAK keys and activation infrastructure
- Limited tooling support: New management features won’t work on EOL systems
More critically, ESU doesn’t solve the EPP problem. If you have Windows 10 systems without endpoint protection today, buying ESU doesn’t deploy an agent. You’re just paying to delay the inevitable while your attack surface remains exposed.
The Solution
If you’re considering ESU, build a realistic TCO model:
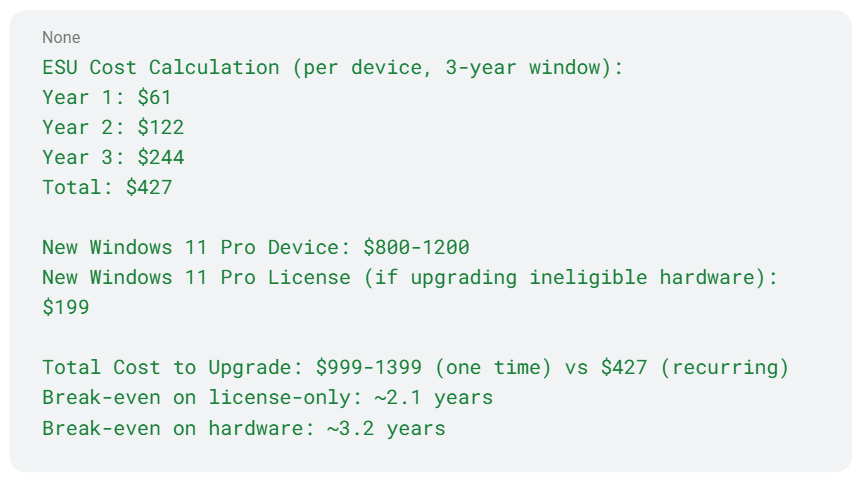
Then factor in the operational burden:
- Help desk time and resources to support aging hardware
- Security team time and resources to manage exceptions
- Compliance risk from unsupported systems
- Opportunity cost of not having modern features
Most organizations find that ESU makes sense for 10-20% of their fleet—specialized systems running legacy applications that can’t upgrade. For general-purpose workstations, particularly those missing EPP, the math doesn’t add up.
Question #3: Are We Creating a Compliance Blind Spot?
Organizations operating under compliance frameworks (PCI DSS, HIPAA, SOC 2, ISO 27001) often don’t realize that running unsupported operating systems can create audit findings—even if you’re on ESU.
Technical Reality
Compliance frameworks increasingly reference vendor support status:
- PCI DSS 4.0 Requirement 6.3.3: “All system components are protected from known vulnerabilities by installing applicable security patches/updates, including (a) Critical or high-security patches within one month, and (b) All other applicable security patches within three months”
- HIPAA Security Rule § 164.308(a)(5): “Implement procedures for guarding against, detecting, and reporting malicious software”
The keyword is “applicable security patches.” When Microsoft stops releasing patches for Windows 10, auditors will ask: “How do you know you’re protected from vulnerabilities you don’t know about yet?”
The Solution
Build compliance documentation into your Windows 10 strategy:
- Create a risk acceptance document for systems remaining on Windows 10:
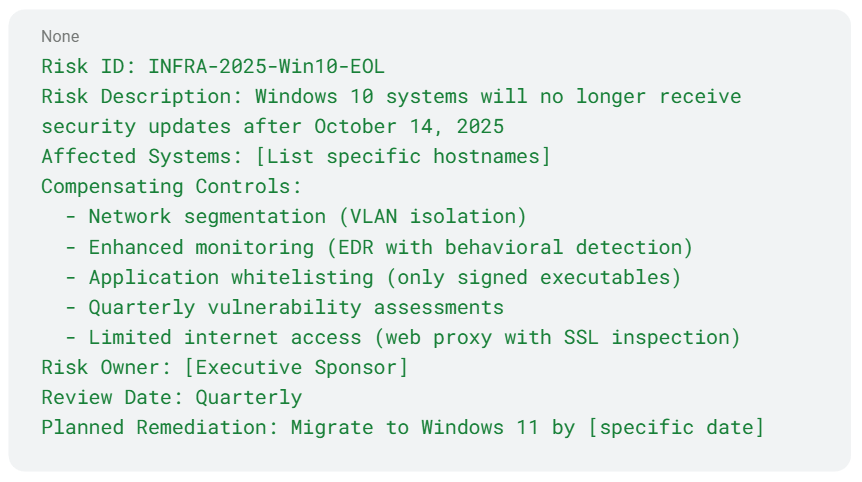
- Implement technical compensating controls, such as:
- Network segmentation
- Application control
- Enhanced logging
- Privileged Access Management (PAM)
- Create audit-ready reports, that are ideally continuously updated via automation or that can be generated on demand:
- Total Windows 10 systems
- Systems isolated via network segmentation
- Systems with EDR in a prevention policy
- Systems with application control
Question #4: Are Our Compensating Controls Actually Compensating?
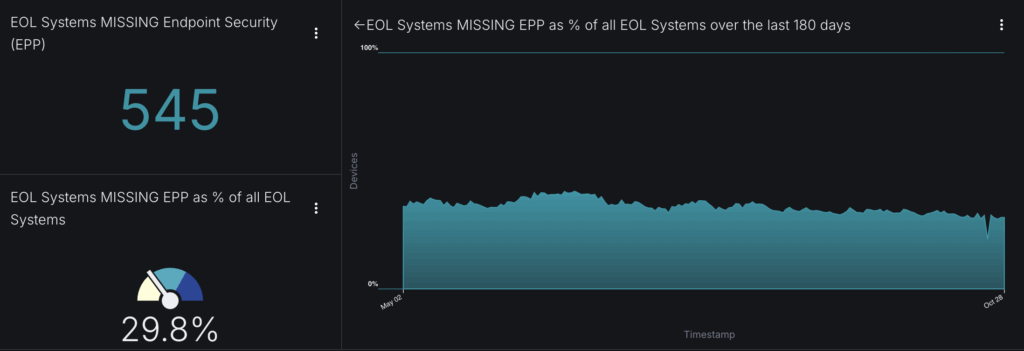
The dashboard above shows 372 Enterprise Endpoints missing EPP—29% of all EOL systems. This is where things get dangerous. 38% of organizations have at least one Windows 10 system without EPP installed at all. These systems make up nearly 4% of all Enterprise Endpoint Desktops.
Technical Reality
There are multiple ways endpoints can be “missing” EPP:
- Never installed: System provisioning failed or wasn’t part of the golden image
- Uninstalled: User removed it, or it conflicted with other software
- Failed agent: Installed but not checking in due to network/certificate/licensing issues
- Excluded from policy: Intentionally excluded for compatibility (and then forgotten)
- Management plane disconnect: Agent running but not reporting to console
The Solution
Deploy a multi-stage verification process, don’t just trust that because an agent is “there” that it’s effectively protecting these systems. You should review or export via API your EPP platforms enrolled devices, then cross-reference against your authoritative device list. Once you believe that is correct, you should review the last time the EPP agents checked in, agent/signature versions, and policy configuration to make sure that the system is healthy. Endpoint agents can often become broken, miss critical updates, or be temporarily moved into incorrect policies.
Question #5: How Do We Prepare for the Future?
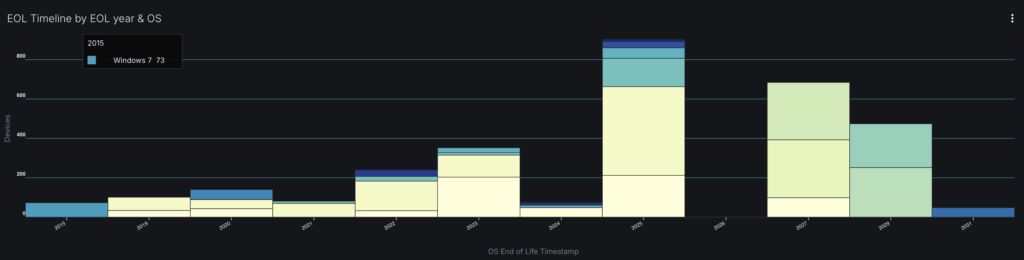
A closer look at the “EOL Timeline by EOL year & OS” chart in the dashboard above reveals something troubling: this organization still has Windows 7 systems still in production—years after EOL. Systems that were end of support in 2015, end of security support in 2020, and whose last Extended Security Update ended in January 2023, running in 2025. This isn’t just one or two forgotten boxes—it’s a persistent tail of legacy systems that never got migrated.
Technical Reality
EOL migration projects fail because:
- Application dependencies: “We can’t upgrade because App X only works on Windows 10”
- Resource constraints: “We don’t have the budget/staff this quarter”
- Scope creep: “While we’re upgrading, let’s also…”
- Poor visibility: “We thought we were done, but missed 200 systems”
- User resistance: “Power users” with local admin who block deployments
- Vendor delays: Waiting for a compatibility update that never comes
The result? October 14, 2025 has come and gone, and 30% of your Enterprise Desktops are still running Windows 10.
The Solution
Build a phased migration plan with technical enforcement that looks forward approximately 12 months:
Phase 1: Discovery and Categorization (Months 1-2) – Inventory systems reaching EOL in the next 12 months and categorize those systems by upgrade readiness. For example, with Windows 10 devices, do my systems meet the requirements to upgrade to Windows 11 (such as TPM)?
Phase 2: Application Testing (Months 2-4) – Create a Windows 11 pilot ring for each department (Engineering, HR, Finance, etc.), upgrade to supported operating systems, and monitor application compatibility for at least 30 days. Use application inventory tools to identify dependencies on existing operating systems.
Phase 3: Staged Migration (Months 4-12) – Use an automated, tiered approach to roll out the supported operating system. This should make sense to your business, but an example could be:
Wave 1: Low-risk systems (kiosks, lab machines) – Months 4-5
Wave 2: Standard users – Months 6-9
Wave 3: Power users and specialized systems – Months 10-12
Phase 4: Enforcement (Month 10+) – As you approach the EOL deadline, implement technical controls, such as a GPO to warn users of the impending deadline or deploy compensating controls to unmigrated systems.
Don’t Let Windows 10 EOL Become Your Next Breach Story
The data doesn’t lie: 76% of organizations still have Windows 10 systems in production, with half of those organizations showing gaps in endpoint protection coverage. The organizations that will successfully navigate Windows 10 EOL are those that can accurately answer these fundamental questions:
- Do we know how many Windows 10 systems we have? And can we maintain an accurate inventory of these systems?
- Do we have an extended support strategy that makes sense? And is it the right decision for our business?
- Are we creating a compliance blind spot? And how can we prepare for future audits?
- Are our compensating controls actually effective? And are they documented and monitored?
- How do we prepare for the future? And how can I stay in front of future migrations?
If you can’t answer those questions with confidence today, you are officially behind the times.
Ready to take command of your Windows 10 EOL migration? See how the Sevco Exposure Assessment platform can help you gain complete visibility into your asset inventory, identify gaps in security controls, track migration progress with confidence—and more. Contact Sevco today.
