If you’re a security analyst, you’ve inevitably wasted hours starting with just an IP address or hostname in a SIEM alert and trying to get more device details. We all know the drill: pivot to the CMDB, check the EDR console, look in Active Directory – all just to figure out what a device is, who owns it, and what its security posture looks like. This initial data gathering is an exhaustingly tedious bottleneck in alert triage – and sometimes dangerously so when reviewing a critical time-sensitive alert.
To help with this common problem, we’ve released a simple, open-source tool: the Sevco for SecOps (sfso) Chrome Extension. It lets you look up device and user information in Sevco from any webpage, including your SIEM console – no matter if you’re using Splunk, Chronicle, Sentinel or any other web-based SIEM. Simply highlight any hostname or IPv4 address, right-click, and look it up:
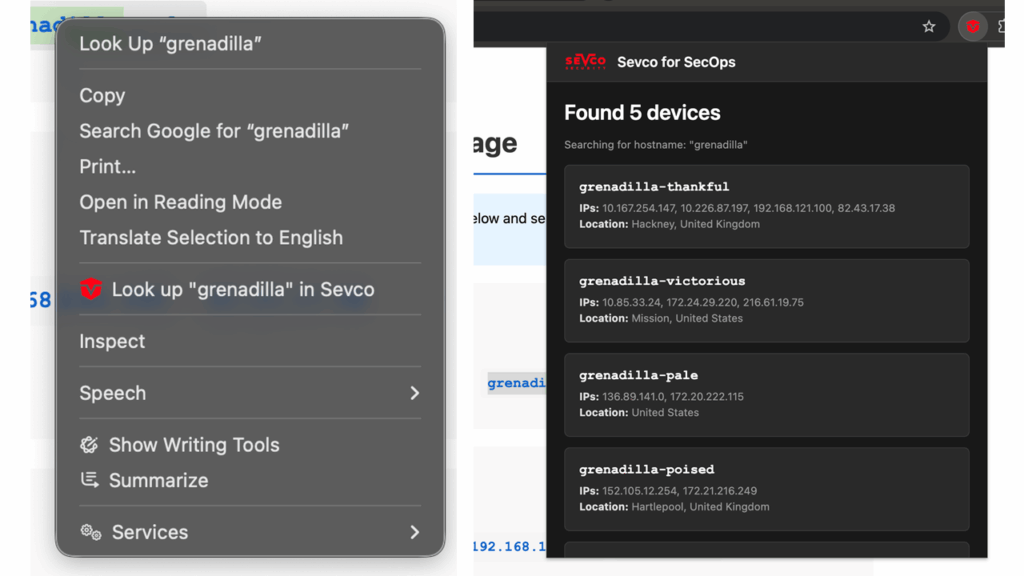
The extension then gives you a quick summary of essential alert context, including:
- Device Details: Operating system, internal and external IP addresses, and last seen timestamps.
- Security Controls: You can immediately see which sources (like your EDR, vulnerability scanner, or patch management) are running on the device and, just as importantly, which ones aren’t. This is great for quickly confirming if a critical control is actually active on the device in question.
- User Context: The summary shows you details of users who have been observed on the device.
- Exposures: You can also see a count of “exposure vulnerabilities” as they are configured in your Sevco instance.
- CVEs: It also includes the total number of CVEs reported on the system by all VA tools that cover the machine, as well as detail for the top ten sorted by CVSS score.
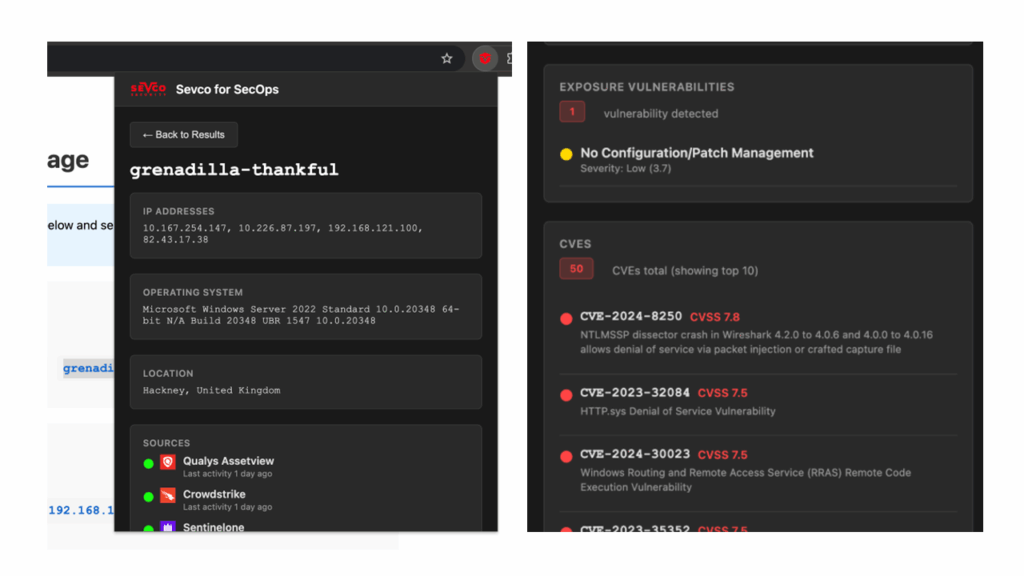
If you need to dig deeper, a single click takes you straight to the full device details in the main console. You can grab the extension from the GitHub repository and install it directly from the source.
Taking it Further: SIEM Integration
While the extension is useful for on-the-fly lookups, the real power of this kind of aggregated asset data comes from integrating it directly into your security tools. For example, the same data that powers this extension can be exported to an AWS S3 bucket and pulled into your SIEM.
This enables more advanced use cases beyond manual triage, allowing you to automate alert enrichment and create more intelligent prioritization rules. For instance, you could build logic to automatically increase the severity of an alert if it fires on:
- A device belonging to a member of your executive team.
- An asset that is missing its EDR agent.
- A server with a high number of critical vulnerabilities.
- …or any combination of the above or an effectively infinite number of other conditions!
For more details on setting up this kind of integration, you can find information in the Sevco documentation on S3 data export or Splunk Inventory Sync, or just contact Sevco support.
Happy hunting!
